About
-
The Central Computer Center of Gautam Buddha University is a central facility that caters the IT needs of the University and provides access to internet resources as well as telecommunication facilities. The Campus network is carefully planned, keeping in view options for future expansions. Fibre-optic cabling is used to connect all the major buildings and Campus is equipped with Wi-Fi connectivity. The CCC has strong IT security infrastructure that protects the University network from cyber attack and other illegal activities.
-
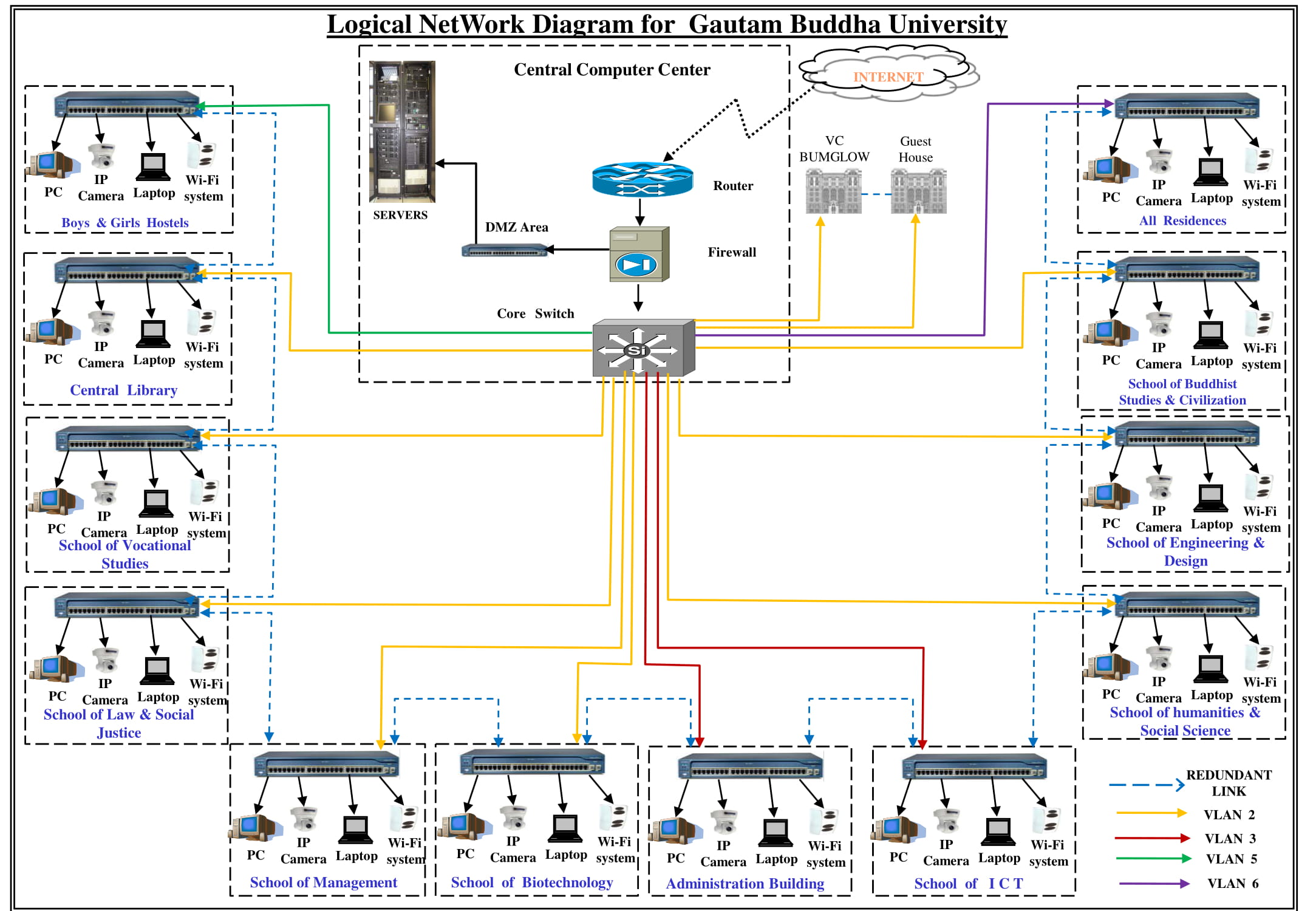
The Campus Network connects to Departments, Schools, Hostels, Hospital, Guest House, etc. LANs connectivity in each area of the network have 10/100/1000 Mbps transmission capacity and are linked through fibre optic cables.
-
Campus has taken 1 Gbps leased line for Internet connectivity from BSNL through NMICT project of MHRD. Bandwidth is distributed to the 10000 nodes in the Campus with Cisco switches. The Campus provides its students the necessary technological skills to upgrade or share their knowledge. A robust campus network is provided to every student for accessing internal servers and the Internet. The Central Computer Centre has power backup through two high end 80KVA UPS and generator set. Air conditioning is provided by the precision AC plant backed-up with VRV AC units. Linux/Windows desktops are provided in all class rooms and labs of different Schools for conducting e-learning and interactive lab sessions during classes.
-
Software for Scientific Computing, Office Automation, and Database Applications are available on various servers. SPSS (Statistical Package for Social Sciences), Prowess (CMIE) are few of scientific libraries available. MATLAB is the application package for scientific applications. Oracle 9i, and SQL SERVER 2008 are the major database packages.
Services
- Central Computer Center (CCC) provides easily accessible and excellent computational facilities to the faculty and students.
- Our entire campus is connected with seamless wireless connectivity using Cisco Access Points.
- Web security Gateway are installed for Malware/ Spyware/virus detection at the gateway level.
- Windows Server update services are installed for Patch Management in the entire campus.
- GBU official website is developed maintained by CCC In-house.
- CCC provides Network, Software & Hardware support.
- Email Service
All University officials, faculty members of Departments and students are provided with Email ID's. All mail services are accessible using Web browser or Gmail app. Email facility is provided to the user by Central Computer Center. All users are given unlimited space for emails storage and Google Drive. Maximum size of outgoing mail can be 30 MB, and the maximum size of incoming mail can be 30 MB.
- Backup and Recovery
The Central Computer Center provides backup of all the systems present in the campus.A user can request for restore of the files available on backup tapes, giving full path names of files/directories to be restored. User can also put request on paper and submit to Central Computer Center.
For Data Backup/Recovery:
Contact No: 0120-234 6237. - Antivirus and Spam Protection
The Central Computer Center provides Anti-virus & Spam Protection at the server and the gateway level for PC's, laptops, email and web services. Additionally, all PCs, laptops in the University and campus that have been provided with connectivity of window update server that updates antivirus automatically on daily basis.
Forms
Servers
The Central Computer Center of Gautam Buddha University consists of the servers to dedicate for important softwares:
- Mail Server
- Web Server
- DNS Server
- DHCP Server
- Windows Update Server
- Application Server
- Libsys Server
- Matlab
- SPSS(Statistical Package for the Social Sciences)
- File Server(FTP)
- Proxy Server
- Backup Server
- Network Monitoring Server
Networks
-
Local Area Network
- All systems are linked by a Giga based Local Area Network. The entire campus has been provided with state of the art network based on Giga cables. It has been extended on optical fiber backbone to cover each and every corner of the University.
- A local area network (LAN) supplies networking capability to a group of computers in close proximity to each other such as in an university building, a school, or residence. A LAN is useful for sharing resources like files, printers, games or other applications.
- A LAN in turn often connects to other LANs, and to the Internet or other WAN. Most local area networks are built with relatively inexpensive hardware such as Ethernet cables, network adapters, and hubs. Wireless LAN and other more advanced LAN hardware options also exist.
-
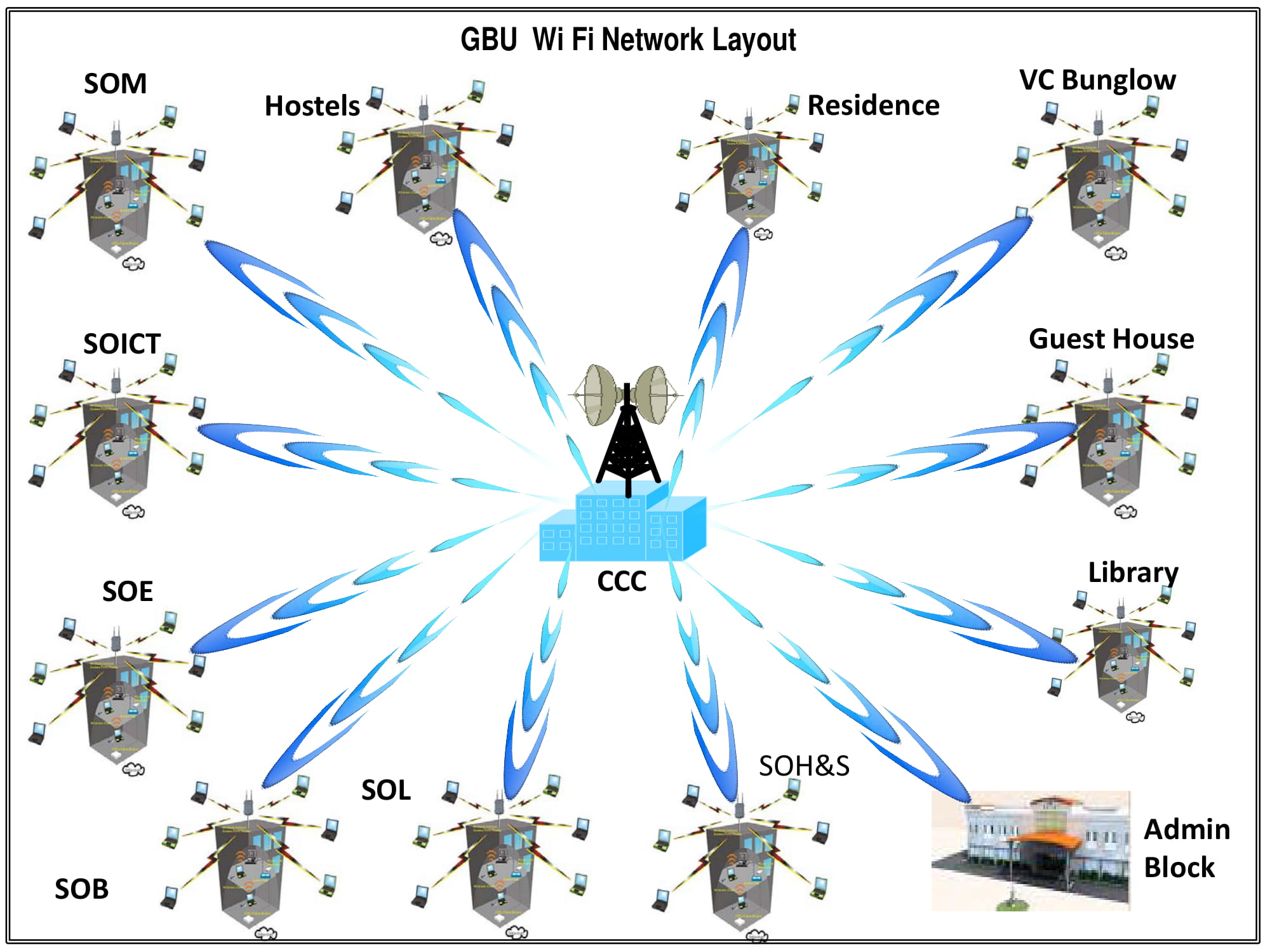
Wireless Networks
- Wireless networks are based on the IEEE 802.11 standards. A basic wireless network consists of multiple stations communicating with radios that broadcast in 2.4GHz.
- 802.11 networks are organized in two ways: in a BSS one station acts as a master with all the other stations associating to it; this is termed infrastructure mode and the master station is termed an access point (AP).
- In BSS mode all communication passes through the AP; even when one station wants to communicate with another wireless station messages must go through the AP. In the second form of network there is no master and stations communicate directly. This form of network is termed an IBSS and is commonly know as an adhoc network.
Lab Policy
The Central Computer Center has made some Lab policies for every student using lab facilities and should follow these facilities. These policies should be strictly followed by all the users if found guilty necessary action would be taken against it.
- The computer lab resources are prohibited from usage for any illegal or disruptive purpose.
- No food or drinks allowed in the computer lab at any time.
- No shouting loud talking or cell phone-alt use allowed inside the labs.
- Students are not permitted to install, modify or delete any software on lab computers.
- Scheduled classes in the lab have priority overall other uses.
- The computer lab is not responsible for problems caused by computer viruses, improper use of the equipment or loss of data due to equipment malfunctions or any others reason.
- Equipment in the computer labs may not be removed, modified, relocated, or disassembled without permission of the lab coordinator.
- Reproduction of any copyrighted material (e.g. Software, Music, Video, Books, Photographs, etc.) is prohibited.
- Displaying of offensive graphic images by way of Web Browser or other software is not permitted.
- Chatting, playing games are not allowed.
- Be respectful of other lab users, lab equipment and area at all time in the computer labs.
- Problems with computer lab equipment and software problem should be reported to the lab personnel immediately.
- Users are expected to keep the computer lab neat and tidy and if needed, should clean up the area around the computer that they used before leaving.
- Protect your security - Log off the computer before leaving the computer lab.
Any physical damage to the system or any lab property will lead to the Punishment as decided by the University Administration. Student who does not follow the above rules will be suspended from the lab for 7 days.
Directory
| Name Designation | Phone No. | Email ID |
|---|---|---|
| Dr. Sandeep Singh Rana (System Manager) | +91 120-234 4246 | sandeep@gbu.ac.in |
| Mrs. Pallavi Upadhyay (Technical Superintendent) | +91 120-234 6232 | pallavi@gbu.ac.in |
| Mr. Raj Kumar (Technical Superintendent) | +91 0120-234 6234 | raj.kumar@gbu.ac.in |
| Mr. Kailash Chand Sharma (Hardware/Software Support) | +91 120-234 6237 | ksharma@gbu.ac.in |
Contact Us

Dr. Sandeep Singh Rana
System Manager
Central Computer Center
Gautam Buddha University
Greater NOIDA
Uttar Pradesh (INDIA) - 201312
0120-234 4246
sandeep@gbu.ac.in
FAQ's
e.g - Browser Hijacker, File Infector, Macro Virus, Polymorphic Virus, Multipartite Virus, Direct Action Virus, Boot Sector Virus, Web Scripting Virus, Memory Resident Virus,FAT Virus
When you share a copy of an infected file with other computer users, running the file may also infect their computers; and files from those computers may spread the infection to yet more computers.
If your computer is infected with a boot sector virus, the virus tries to write copies of itself to the system areas of floppy disks and hard disks, Then the infected floppy disks may infect other computers that boot from them, and the virus copy on the hard disk will try to infect still more floppies.
- Without harping on the subject - keep your antivirus up to date and protect yourself from trojans!
- If you must store personal information on your machine, encrypt it.
- Use strong passwords, that is: Use minimum 8 characters long combination of Alpha-Numeric and Special symbols meaningless words (e.g. A@20$z_Y).
- Keep your Operating System and Applications up to date and patched against the latest discovered vulnerabilities.
- Do not run files that are sent to you, unless you are completely sure of their integrity.
- Do not click on hyperlinks from people you don't know.
- Install a firewall application, particularly if you are connected to internet.
- Ensure that the browser you use supports security and is capable of encrypting information that you may send.
- If you are getting rid of an old machine, ensure that you have wiped the hard disk (using a wiping utility) deleting the files is not precaution enough.
- Read website security and privacy policies.

OR
Open Command Prompt (cmd) ->
Type ipconfig/all and Press Enter key.
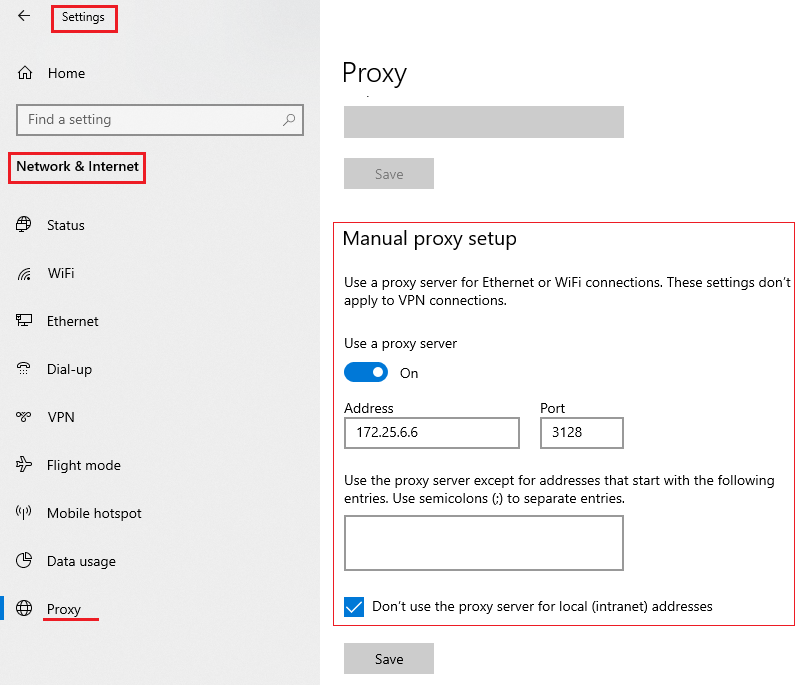
Open Settings -> Network Internet -> Proxy
172.25.6.6 3128
For Google Chrome -
Open Google Chrome -> Settings -> Advanced -> System - Open proxy settings -> Connections - LAN Settings
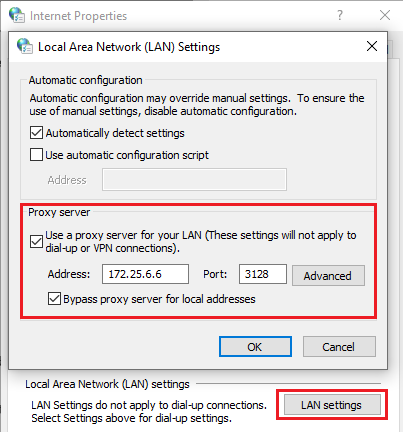
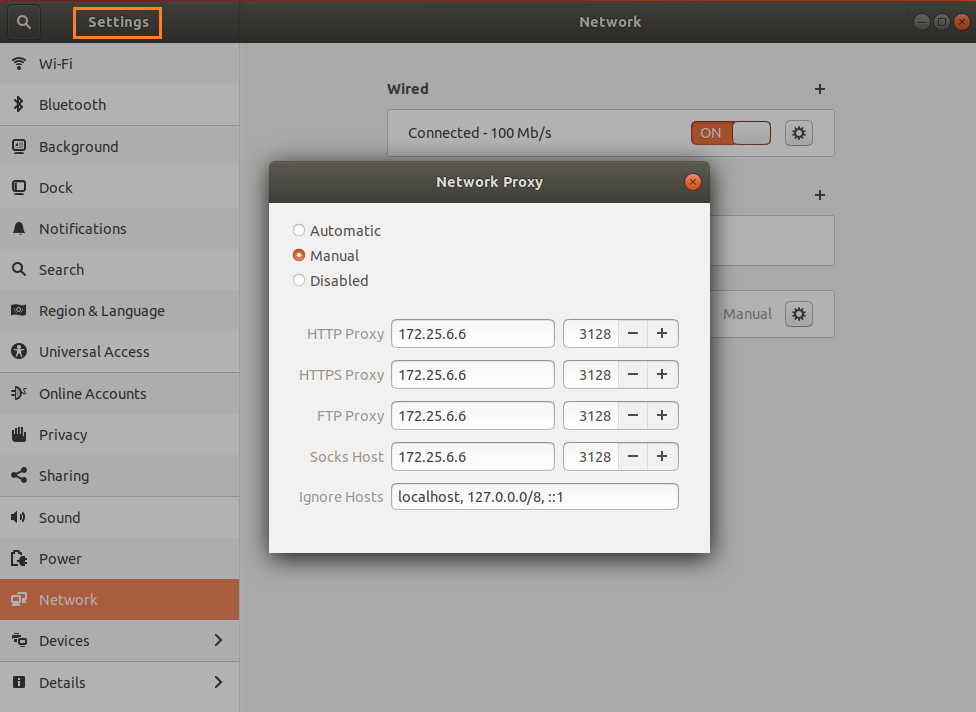
For Ubuntu -
Open Settings -> Network -> Network Proxy -> Select Manual